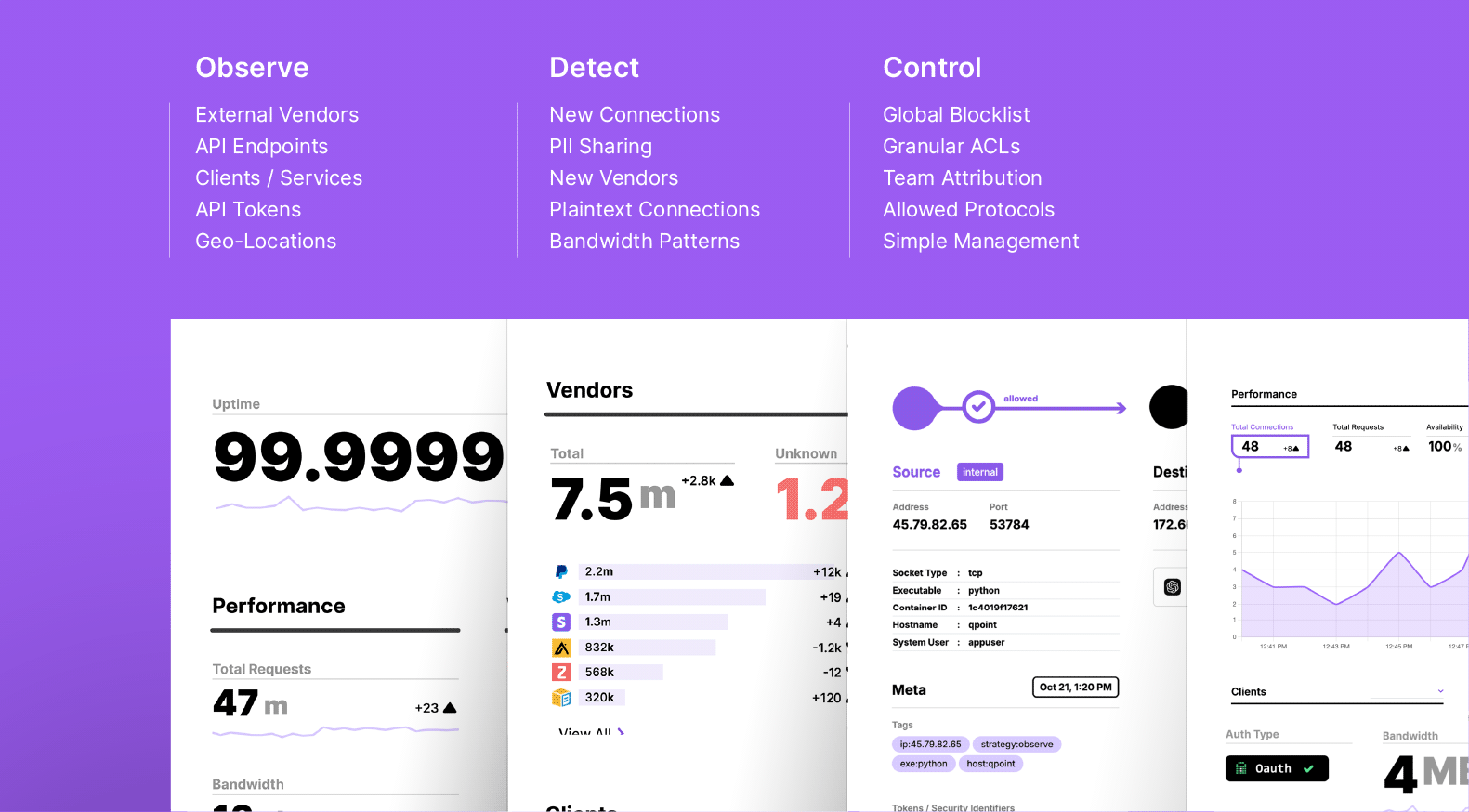
Unveiling Q.Tap Open SourceSecurity Observability for the Encrypted Cloud

Today, I'm thrilled to announce the open-source release of Q.Tap - our eBPF powered agent that transforms security observability by providing visibility into encrypted traffic without proxies, code changes, or complex installations.
The Journey: Why We Built Q.Tap
Our journey began like many others in the observability space - with a proxy. We initially believed that intercepting and inspecting traffic through a man-in-the-middle approach was the only viable solution to gain visibility into traffic destined for service dependencies.
But as we engaged with the industry and listened to our users, a clear pattern emerged: while organizations desperately needed visibility into their encrypted traffic, they were frustrated with the operational overhead of managing certificates, configuring proxies, and maintaining yet another component in their already complex architectures. The feedback was consistent:
"Certificate management is a nightmare."
"We need visibility, but we can't afford the latency impact."
"Deploying proxies across our entire infrastructure is too resource-intensive."
The Pivot: From Proxy to eBPF
This feedback pushed us to rethink our approach fundamentally. What if we could provide the visibility teams needed without the proxy headache? What if we could tap into encrypted traffic before it even gets encrypted?
Enter Q.Tap - our OpenSSL-focused solution that leverages the power of eBPF to capture critical request/response details pre-encryption, directly from the kernel.
The key insight that drove our development was simple: we don't need to decrypt traffic if we can observe it before encryption occurs. By hooking into OpenSSL at the library level, Q.Tap provides all the visibility of a proxy with none of the operational overhead.
Cloud Complexity & Encryption Hide Critical Security Information
Without the full picture, security teams are forced to rely on static, out-of-date, and often incomplete information about what's happening in their environments. This creates multiple critical blind spots:
Undocumented External Dependencies: We're identifying untracked shadow APIs and services that could lead to supply chain attacks or outages when compromised.
Sensitive Data Exfiltration: We're detecting when PII, credentials, or other sensitive data is being sent to unauthorized endpoints, indicating potential data leaks or misconfigured applications.
Misconfigured Egress Policies: We're highlighting overly permissive outbound traffic rules that allow connections to malicious domains, increasing the risk of data breaches.
Unauthorized API Access: We're identifying API calls using improper or compromised credentials, which could indicate credential stuffing or stolen keys.
Our customers were struggling with these challenges daily, and traditional solutions were falling short.
How Q.Tap Works
Unlike traditional proxies that sit in the network path and require certificate management, Q.Tap works by:
Deploying a lightweight eBPF agent that attaches to OpenSSL calls
Capturing traffic before encryption occurs
Providing detailed visibility into requests and responses without affecting the encryption process
Requiring zero configuration changes to applications or network
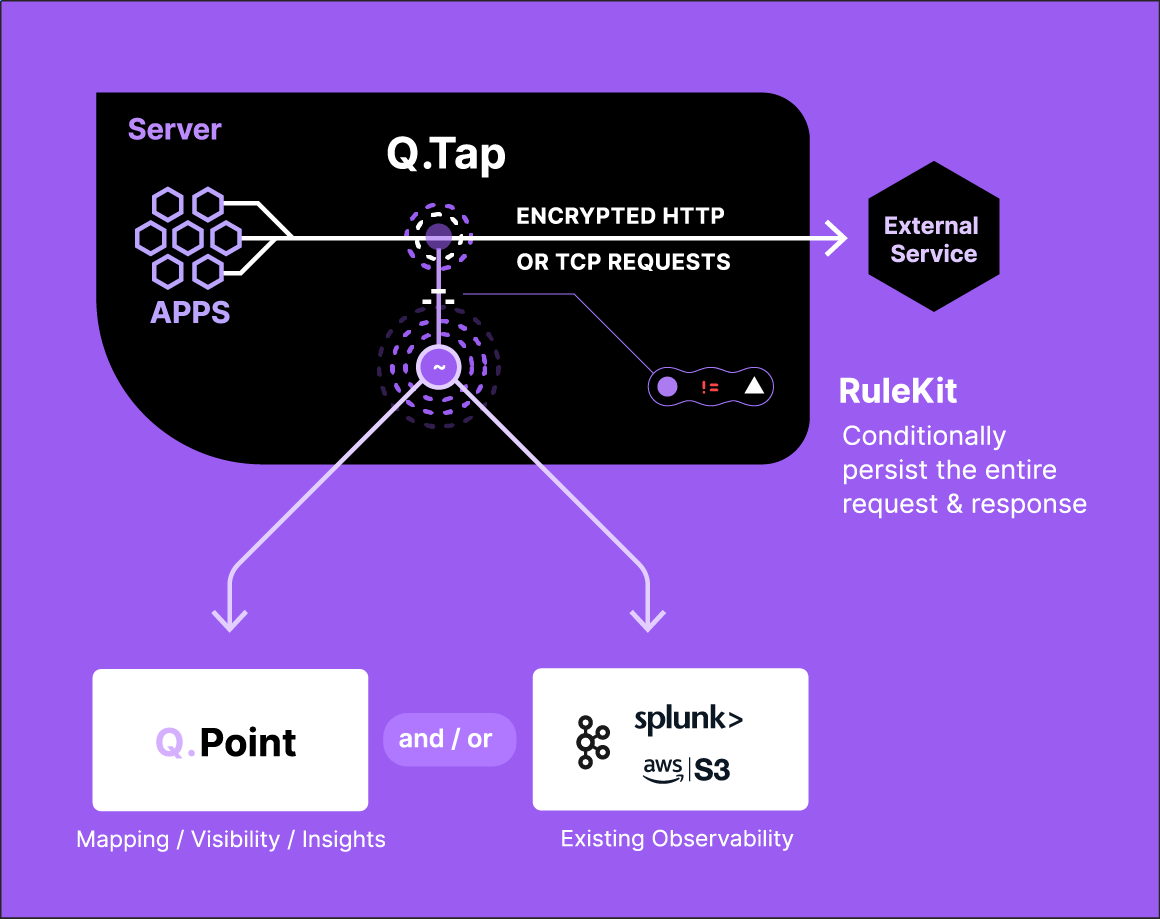
The result? Complete visibility into encrypted traffic without the need to manage certificates, configure proxies, or modify application code.
The Qpoint Security Solution: Zero Instrumentation
Q.Tap delivers five key capabilities that transform security observability:
See Through Encrypted Traffic: We capture critical request/response details pre-encryption—no TLS termination or certificate management required. This means you can finally see what's in those encrypted payloads without compromising your security model.
Automatically Discover Dependencies & External Integrations: We map all dependencies and external connections, with full attribution to show what's connecting and which teams own them. No more surprise integrations or shadow IT.
Identify PII & Sensitive Data Sharing: We verify that sensitive data (like PII or financial information) isn't being inadvertently transmitted, helping meet regulatory requirements like GDPR or PCI-DSS.
Realtime Alerts When Anything Changes: Don't wait to be told about new vendors, integrations, or sensitive data exfiltration routes. Get realtime alerts whenever anything changes in your environment.
Enforce Safe Egress Controls: Implement granular egress control policies directly at the source, safeguarding AI workloads and data exfiltration routes.
Why Open Source?
We've decided to release Q.Tap as an open-source solution for the OpenSSL library because we believe that basic visibility into encrypted traffic shouldn't be a luxury - it should be accessible to everyone. Our commercial offerings will extend support to other TLS implementations (GoTLS, NodeTLS, JavaSSL) while providing additional enterprise features.
Beyond Q.Tap: The Qpoint Platform
While Q.Tap solves the immediate challenge of encrypted traffic visibility, it's just one component of our broader Qpoint platform, which addresses the full spectrum of service dependency challenges:
- Discovering and mapping dependencies across your entire ecosystem
- Resolving issues 10-20x faster with precise attribution and unified visibility
- Enforcing granular access control policies directly at the source
- Safeguarding AI workloads with real-time governance
Get Started Today
Ready to try Q.Tap? Visit our GitHub repository at https://github.com/qpoint-io/qtap to download, install, and start gaining visibility into your encrypted traffic within minutes.
Join us on this journey to make service dependencies visible, controllable, and secure - without the proxy headache.
Qpoint: Security Observability for the Encrypted Cloud - No Proxies, No Code Changes, Simple Installation